LDAP Settings
Introduction
If an organization has LDAP server configured at its end and maintains its users’ data in LDAP, then QMetry supports LDAP integration to import such users into QMetry application. User authentication from LDAP/Active Directory as well as from QMetry database is provided considering existence of both kinds of users in the same organization. For example, an organization can have a large number of users in QMetry that are authenticated through their Active Directory and at the same time, can have a good number of users who do not have their accounts in the Active Directory.
Authenticate and Import LDAP Users
The LDAP (Lightweight Directory Access Protocol) feature allows LDAP users to import themselves into QMetry database. The Admin needs to do the initial settings in Integration > LDAP. The LDAP should be “Active” to define the authentication type as LDAP.
Note: Only one LDAP AD can be integrated with QMetry for authentication.
Admin credentials are now optional to set up LDAP in order to enable anonymous search for users to import. If your LDAP allows anonymous queries, you can proceed without entering the Admin username and password on the settings screen.
Individual LDAP users will be added in QMetry database when they log into QMetry. Bulk users can not be imported at once because it may cause hanging QMetry during the process.
Admin’s credentials are made non mandatory.
Use Case: The Administrator does not want to enter Admin’s username and password in the fields, and save the credentials in the system. As their LDAP allows anonymous queries, they prefer to have the fields non mandatory.
How does the functionality work?
When a user logs into QMetry for the first time with his LDAP credentials, the system first checks existence of the user in QMetry database. If the user exists in the database, then this user is authenticated using QMetry database. If the user does not exist in the QMetry database, then the credentials entered by the user are sent to the LDAP Active Directory. If the LDAP / Active Directory responds positively, the user will be added to the QMetry database. Default Project and default user role are assigned to this user to let him access QMetry.
Now next time when LDAP user logs into QMetry using LDAP credentials, the credentials are sent to LDAP / Active Directory for authentication as the user has already been added in the database. The user is allowed to access QMetry on receiving positive authentication from LDAP.
The new functionality works with different approach in different scenarios as mentioned below.
| Scenario | The user has an account in - | Authentication Type is set as - | Result when the user tries to log into QMetry - |
| 1 | QMetry database | QMetry | QMetry will authenticate the user against QMetry database. If the match is found, the user will be able to log into QMetry. |
| 2 | QMetry database | LDAP | QMetry will authenticate that user against the LDAP/AD. If the match found, the user will be able to log into QMetry. This scenario is only valid when LDAP is active. |
| 3 | LDAP | LDAP | QMetry will authenticate that user against the LDAP/AD. If the user is authenticated successfully, the user’s account will be created in QMetry having Authentication Type “LDAP”.Once the user is created in QMetry, default Project and default role is assigned to that user to let him log into QMetry. Access will be automatically provided to the default Projects with default assigned role. |
If the user doesn't have an account in QMetry and also in the LDAP, then create an account for this user locally in QMetry. The user account will be added in QMetry database with Authentication Type “QMetry”. The user will be able to log into QMetry then.
LDAP/AD password is handled by LDAP/AD server. So LDAP/AD users need to contact their network administrator for any password related issues like Reset Password, Forget Password and Update Password. Other (non LDAP/AD) users can reset their password as usual through QMetry.
Ways to Authenticate LDAP Users
Manual User Authentication
In this method, Admin needs to manually add LDAP users and assign them Project and corresponding role manually for security purpose and better controls of QMetry instance.
Steps for Admin to follow:
- Make sure your LDAP settings are Active.
- Make sure your QMetry instance do not have any default Project assigned for new LDAP users.
- Make sure your QMetry instance do not have any default role assigned for new LDAP users.
To add a new LDAP user follow the steps below:
- Go to Customization > Users. Enter Login Id of the user which is same as LDAP Username and add other details.
- Set Authentication Type as "LDAP".
- Click Save. The new user is added successfully but at this point there is no Project or role assigned to them.
- Now go to Customization > Users. Edit the User and assign Projects and Roles to that user.
- Once this is done, ask your LDAP users to log in.
Automatic User Authentication
In this method, Admin needs to set default settings for new LDAP user by assigning them a default role and Project. Once the settings are done there is no manual intervention required from admin. LDAP users are authenticated automatically.
Steps for Admin to follow:
- Make sure your LDAP settings are Active.
- Set default Project assigned for new LDAP users. Following settings are required for it.
- Go to Projects > Project/Release/Cycle. Open create screen or edit screen of project.
- (Option) Add in LDAP/SAML by Default: Turn the flag On to assign this Project as default to the new LDAP users.
- Set default role assigned for new LDAP users. Following settings are required for it.
- Go to Customization > Roles. Open Create screen or Edit screen of role.
- (Option) Make this the default role for new LDAP/SAML users: Turn the flag On to assign this Role as default role to every new LDAP/SAML user.
For example, The “Tester” role is assigned as default role to the LDAP users when they log into QMetry the first time. You can assign different role later on. Only one role can be assigned as default role. So the role selected last will override the role assigned earlier. You can assign multiple Projects with a single User Role to the LDAP users. A warning message pops up when you are going to unassign that single assigned role.
Once the settings are done from Admin side, LDAP users can directly log into QMetry and are assigned default roles and Projects automatically.
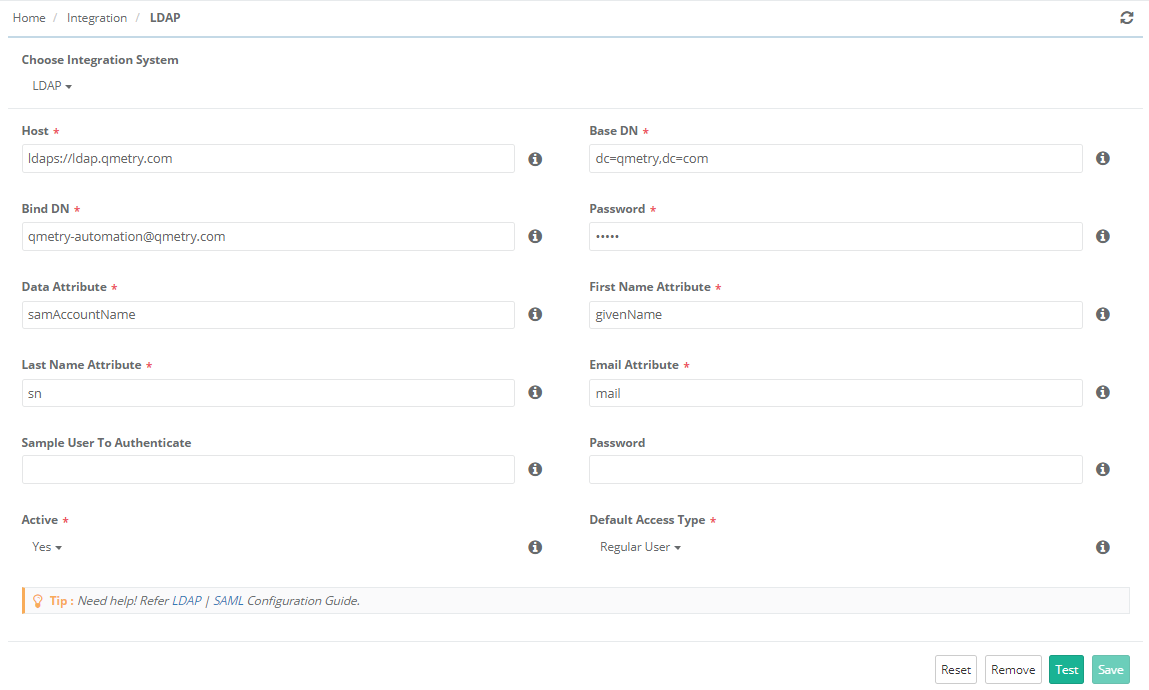
LDAP Configuration
Go to Integration > LDAP/SAML.
Select LDAP as Integration System on the next screen.
Provide details mentioned below to configure LDAP Settings:
- Host: The URL contains IP of the machine where LDAP server is configured and universal LDAP Port No. 389 in the following format:
ldap://<IPAddress>:<Port No.>
LDAP Integration also supports HTTPS protocol. So the Host format could be
ldaps:// <IPAddress>:<Port No.>
- Base DN: Specify Base DN values in appropriate format e.g. dc=qmetry, dc=com
- Bind DN: This is the username of the person (i.e., admin of the QMetry instance) who is going to import LDAP users. If you need to authenticate to search for users, log in as this user. You can leave the field blank for anonymous search.
E.g., cn=example, cn=users, dc=example, dc=com
(Note: This is not a mandatory field. You can keep the field blank if your LDAP allows anonymous queries.)
- Password: This is the password for the username above. If you need to authenticate to search for users, use this password. You can leave the field blank for anonymous search. (Note: This is not a mandatory field. You can keep the field blank if your LDAP allows anonymous queries.)
Notes:
- If the Admin credentials are changed but are not updated in the QMetry settings, then the LDAP users will not be able to log into QMetry.
- Make sure your password is not getting expired automatically at certain intervals. Else, you will have to change the password in this field correspondingly.
- Data Attribute: The field where QMetry Login field is stored.
- First Name Attribute: The attribute in LDAP containing the first name. (If attribute is empty, Data attribute will be used.)
- Last Name Attribute: The attribute in LDAP containing the last name. (If attribute is empty, Data attribute will be used.)
- Email Attribute: The attribute in LDAP containing the email name. (If attribute is empty, Data attribute will be used.)
- Sample User Name to Authenticate: This is an optional field to test LDAP server integration once connected. Give sample user name i.e. email address of LDAP user to be authenticated to verify the connection.
- Sample User’s Password: This is an optional field. If Sample User Name is mentioned above then provide corresponding password in this field.
- Active: The drop down menu has two options on it to select from: Yes, No
If the Active field is set as “Yes”, then only the Authentication Type in Customization > Users could be set as “LDAP” and the users will be able to log in with their LDAP password only.
If the Active field is set as “No”, then the Authentication Type in Customization > Users could be set as “QMetry”. Users are authenticated against QMetry database for login.
- Default Access Type: In case of LDAP users, Default Access Type is configured from Integration > LDAP. While importing users through LDAP, the Default Access Type will be assigned based on this settings.
Sample Settings Parameters
| Active Directory Details: (on Windows) | LDAP Directory Details: (on Linux) |
| Host: 10.12.51.4 | Host: ldap://10.12.51.238:389 ldaps://10.12.51.238:636 |
| Base DN: DC=qmetry,DC=com | Base DN: dc=qmetry,dc=com |
| Bind DN: CN=joseph,OU=sales,DC=qmetry,DC=com | BindDN: uid=root,ou=users,dc=qmetry,dc=com |
| Data Attribute: sAMAccountName | Password: redhat Data Attribute: uid Sample User: leesa.mathew@qmetry.com Sample User Password: leesa123 |
There are two buttons on the page:
- Test: It authenticates the user whose password is provided in the Password field and who tries to import the user(s) from the LDAP Server. Click the Test button to verify the connection with the server. A message window pops up.
- Save: Click the Save button to store the LDAP details into the database. A message window pops up.
Authentication Type for the user is set from Customization > Users.
Default Projects are assigned from Projects > Project/Release/Cycle.
Default Roles are assigned from Customization > Roles.
Note: LDAP users can log in without organization code for on-premise installations.